某计算机系统中有一个CPU、一台输入设备和一台输出设备,假设系统中有四个作业T1、T2、T3和T4,系统采用优先级调度,且T1的优先级>T2的优先级>T3的优先级>T4的优先级。每个作业具有三个程序段:输入Ii、计算Ci和输出Pi(i=1,2,3,4),其执行顺序为Ii→Ci→Pi。这四个作业各程序段并发执行的前驱图如下所示。图中④、⑤、⑥分别为( )。
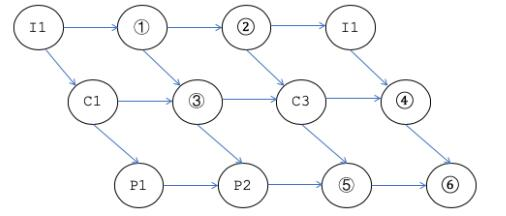
- A.C2、C4、P4
- B.I2、I3、C4
- C.I3、P3、P4
- D.C4、P3、P4
正确答案及解析
正确答案
解析
前趋图是一个有向无循环图,由节点和有向边组成,节点代表各程序段的操作,而节点间的有向边表示两个程序段操作之间存在的前趋关系(“→”)。程序段Pi和Pj的前趋关系可表示成Pi→Pj,其中Pi是Pj的前趋,Pj是Pi的后继,其含义是Pi执行结束后Pj才能执行。本题完整的前趋图如下图所示,具体分析如下。
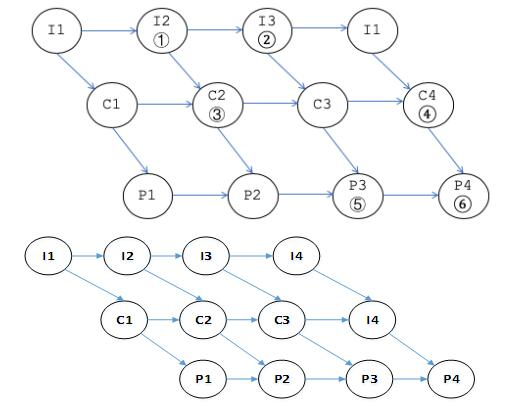
根据题意,I1执行结束后C1才能执行,C1执行结束后P1才能执行,因此I1是C1、P1的前趋,C1是P1的前趋。可见,图中③应为C1。又因为计算机系统中只有一台输入设备,所以I1执行结束后I2和I3才能执行,故I1是I2和I3的前趋,I2是I3的前趋。可见,图中①、②分别为I2、I3。根据题意,I4、C3执行结束后C4才能执行,即I4、C3是C4的前趋,所以④应为C4。又因为计算机系统中只有一个CPU和一台输出设备,所以C3、P2执行结束后P3才能执行,C3、P2是P3的前趋;同理C4、P3执行结束后P4才能执行,C4、P3是P4的前趋。经分析可知图中⑤、⑥分别为P3、P4。计算机系统中只有一个CPU,而且系统采用优先级调度,所以C1是C2的前趋,C2是C3的前趋。可见,图中④应为C4。
包含此试题的试卷
你可能感兴趣的试题
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like (作答此空),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.compression
- B.encryption
- C.decryption
- D.translation
- 查看答案
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should (作答此空)the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.address
- B.define
- C.ignore
- D.pose
- 查看答案
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational (作答此空)and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.behaviors
- B.cultures
- C.policies
- D.structures
- 查看答案
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the (作答此空)security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.logical
- B.physical
- C.network
- D.Information
- 查看答案
Data security is the practice of protecting digital information from (作答此空)access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.unauthorizeD
- B.authorizeD
- C.normal
- D.frequent
- 查看答案