阅读下列说明,回答问题1至问题4,将解答填入答题纸的对应栏内。【说明】项目组成员小张根据项目经理的要求绘制了项目A的WBS图(如下),并根据工作量对项目的成本进行了分配,见下表。
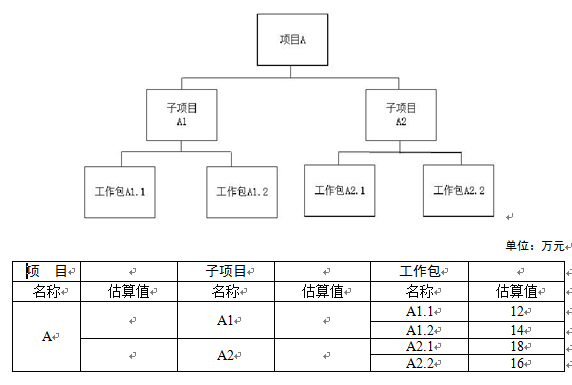
【问题1】(3分)如果小张采取自下而上的估算方法。请计算A1、A2、A的估算值分别是多少?【问题2】(10分)在进行项目预算审批时,财务总监之处在2012年初公司实施过一个类似项目,当时的决算金额是50万元,考虑到物价因素增加10%也是可接受的,财务总监要求据此更改预算,请根据财务总监的建议列出A1、A2、A1.1、A2.1的估算值以及项目的总预算。【问题3】(3分)项目经理认为该项目与公司2012年初实施的一个类似项目还是有一定区别的,为稳妥起见,就项目预算事宜1,项目经理可以向公司财务总监提出何种建议。【问题4】(9分)除了自下而上的估算方法,本案例还应用了哪些成本估算方法?成本估算的工具和技术还有哪些?
正确答案及解析
正确答案
解析
【问题1】A1的估算值=12+14=26(万元);A2的估算值=18+16=34(万元);A的估算值=26+34=60(万元)。【问题2】根据总监的建议:A1估算值=55 ? 26/60=23.83(万元);A2估算值=55 ? 34/60=31.17(万元);A1.1估算值=55 ? 12/60=11(万元);A2.1估算值=55 ? 18/60=16.5(万元);2013的总预算=50 ? 1.1=55(万元)。【问题3】建议:1)根据项目WBS的具体情况,对预算做出调整;2)类比估算由于项目的一次性,独特性等特点,实际根本不存在完全相同的项目,这种估算准确性比较差,具体到项目执行时,可能根据项目的具体情况,适当调整项目预算。【问题4】1)还用了类比估算法、参数估算法;2)成本估算的工具和技术还有确定资源费率法、准备金分析,质量成本,项目管理软件,卖方投标分析。
你可能感兴趣的试题
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like (作答此空),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.compression
- B.encryption
- C.decryption
- D.translation
- 查看答案
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should (作答此空)the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.address
- B.define
- C.ignore
- D.pose
- 查看答案
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational (作答此空)and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.behaviors
- B.cultures
- C.policies
- D.structures
- 查看答案
Data security is the practice of protecting digital information from ( )access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the (作答此空)security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.logical
- B.physical
- C.network
- D.Information
- 查看答案
Data security is the practice of protecting digital information from (作答此空)access,corruption,or theft throughout its entire lifecycle. It is a concept that encompasses every aspect of information security from the ( )security of hardware and storage devices to administrative and access controls,as well as the logical security of software applications. It also includes organizational ( )and procedures.Data security involves deploying tools and technologies that enhance the organization's visibility into where its critical data resides and how it is used. These tools and technologies should ( )the growing challenges inherent in securing today's complex distributed,hybrid,and/or multicloud computing environments.Ideally,these tools should be able to apply protections like ( ),data masking,and redaction of sensitive files, and should automate reporting to streamline audits and adhering to regulatory requirements.
-
- A.unauthorizeD
- B.authorizeD
- C.normal
- D.frequent
- 查看答案